What is Ransomware?
Ransomware is a type of malicious software that is designed to encrypt files on a computer or network and demand payment in exchange for the decryption key needed to unlock the files. Ransomware attacks have become increasingly common in recent years and have caused significant damage to individuals, businesses, and government organizations.
Table of Contents
How do Ransomware attacks happen?
Ransomware attacks typically occur when malicious software, also known as malware, infects a computer or network. This malware then encrypts the victim’s files, rendering them inaccessible, and demands payment from the victim in exchange for a decryption key to unlock the files.
Ransomware attacks can occur in several ways, including:
- Email phishing: Attackers can send emails with malicious attachments or links that, when clicked, download ransomware onto the victim’s device.
- Malicious websites: Attackers can create fake websites or ads that, when clicked, can download ransomware onto the victim’s device.
- Exploiting software vulnerabilities: Attackers can exploit vulnerabilities in software or operating systems to gain access to a victim’s device and install ransomware.
Why are ransomware attacks on the rise?
Ransomware attacks have been on the rise in recent years due to several factors. Firstly, the increasing reliance on technology and digital systems has created more opportunities for cybercriminals to exploit vulnerabilities in software and networks. Additionally, the anonymity and ease of use of cryptocurrencies have made it easier for attackers to demand and receive ransom payments without being traced. Furthermore, the widespread use of remote work due to the COVID-19 pandemic has increased the attack surface and created new vulnerabilities for cybercriminals to exploit.
The increasing sophistication of ransomware attacks, with some attackers using advanced techniques such as zero-day exploits and social engineering tactics, has made it harder for organizations to defend against these threats. As a result, organizations must be vigilant in protecting their systems and data from ransomware attacks, using a multi-layered approach that includes regular backups, security training for employees, and up-to-date security software.
Why are ransomware attacks so successful?
Ransomware attacks are also successful because they can be difficult to detect and mitigate. In many cases, the attacker can remain hidden in the system for weeks or even months, making it harder for organizations to detect and respond to the attack. Additionally, attackers often use strong encryption to lock the victim’s files, making it nearly impossible to recover them without paying the ransom.
Moreover, ransomware attacks are successful because victims often feel compelled to pay the ransom. Attackers use fear, urgency, and the potential loss of critical data to coerce victims into paying the ransom. Furthermore, the use of cryptocurrencies for ransom payments allows attackers to remain anonymous and untraceable, making it easier for them to get away with the crime.
Royal Ransomware
Royal Ransomware is a type of ransomware that was first discovered in June 2021. It is a variant of the popular STOP/Djvu ransomware family, which has been responsible for many high-profile attacks over the years. Royal Ransomware is typically spread through phishing emails or by exploiting vulnerabilities in outdated software or operating systems.
Royal Ransomware is malicious software that encrypts the files on a victim’s system and demands a ransom in Bitcoin for decrypting them. The ransomware also threatens to leak the data into the public domain if the payment is not made. Royal Ransomware has been targeting multiple critical sectors, including manufacturing, communications, healthcare, education, etc., or individuals since January 2022.
Once installed on a victim’s computer, Royal Ransomware will begin encrypting files and appending the “. Royal” extension to the file names. It will also create a ransom note in each folder that contains encrypted files, with instructions on how to contact the attackers and pay the ransom. The attackers typically demand payment in Bitcoin or other cryptocurrency, and the amount can range from a few hundred to several thousand dollars.
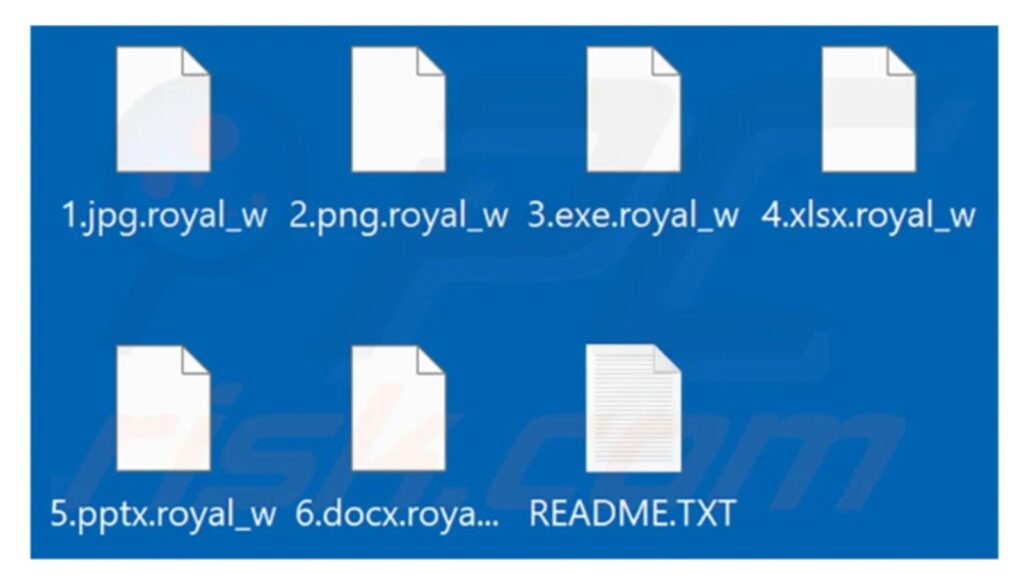
One of the unique features of Royal Ransomware is that it uses a sophisticated encryption algorithm to make it difficult for victims to recover their files without paying the ransom. The attackers also use a custom decryption tool that they provide to victims after they have paid the ransom. However, there is no guarantee that the decryption tool will work, and there have been cases where victims have paid the ransom but still cannot access their files.
The ransomware sneaks in through phishing emails, malicious downloads, abusing RDP (remote desktop protocol), and other forms of social engineering. It uses the OpenSSL library to encrypt files with AES standards and adds a .royal extension to them. It also deletes the volume shadow copies to prevent recovery through service. The ransomware exfiltrates a large amount of data before encryption.
Major Attacks by Royal Ransomware
One of the most notorious ransomware families is Royal Ransomware, which has been active since 2021 and has launched several major attacks on various sectors and regions. We will review some of the most significant incidents involving Royal Ransomware and discuss how to protect yourself from this threat.
- The first major attack of Royal Ransomware occurred in June 2021, when it targeted the Colonial Pipeline, a major fuel supplier in the United States. The attack disrupted the pipeline’s operations for several days, causing fuel shortages and price spikes in some states. The attackers reportedly demanded $4.4 million in Bitcoin for the decryption key, which the company paid.
- The second major attack of Royal Ransomware happened in July 2021, when it infected thousands of computers across 17 countries, including Germany, France, Spain, Italy, and Japan. The attack was carried out through a compromised software update from Kaseya, a provider of IT management solutions. The attackers demanded $70 million in Bitcoin for a universal decryption tool, which they later lowered to $50 million.
- The third major attack of Royal Ransomware took place in October 2021, when it hit the National Health Service (NHS) in England, affecting hundreds of hospitals and clinics. The attack paralyzed the healthcare system for several hours, delaying surgeries and appointments and forcing some patients to be diverted to other facilities. The attackers demanded $20 million in Bitcoin for the decryption key, which the NHS refused to pay.
These three attacks demonstrate the severity and sophistication of Royal Ransomware, which uses advanced encryption algorithms, evasion techniques, and social engineering tactics to infect and extort its victims. The attackers also use various channels to communicate with their victims, such as email, phone calls, and dark web forums.
Are you located Coimbatore? If yes then check out the -> Cyber security training in coimbatore
Impact and Warning About Royal Ransomware by CRET India
The impact of Royal Ransomware has been severe and widespread. According to the Indian Computer Emergency Response Team or CERT-In, Royal Ransomware has attacked critical infrastructure sectors in India and sought pay-off in Bitcoins for not leaking personal data in the public domain. The victims of Royal Ransomware include All India Medical Institute of Medical Sciences, which suffered a major ransomware breach that rendered several of its services inaccessible, also several Indonesian government websites that were targeted by Indonesian hacktivists.
Where to report ransomware attacks in India?
If you are a victim of a ransomware attack in India, you can report the crime to the following authorities:
- Cyber Crime Cell of the local police: The Cyber Crime Cells in various cities and states of India are responsible for investigating cybercrime incidents, including ransomware attacks. You can file a complaint with the Cyber Crime Cell of the local police station in person or online.
- Indian Computer Emergency Response Team (CERT-In): CERT-In is the national nodal agency for responding to cybersecurity incidents in India. They handle cybersecurity incidents of national significance and provide cybersecurity awareness and training programs. You can report a ransomware attack to CERT-In by filling out an incident reporting form on their website.
- National Cyber Crime Reporting Portal: The Ministry of Home Affairs, Government of India, has launched a National Cyber Crime Reporting Portal to report all types of cybercrime, including ransomware attacks. You can file a complaint on the portal, which will be forwarded to the concerned law enforcement agency.
It is important to report a ransomware attack to the appropriate authorities as soon as possible to increase the chances of identifying and prosecuting the attackers and to prevent further damage.
How to check a Ransomware attack on a PC?

There are several signs that your PC may have been infected by ransomware. Here are some of the most common symptoms to look out for:
- Locked or encrypted files: Ransomware attacks usually lock or encrypt files on the infected PC. If you are unable to access your files or if you see unfamiliar file extensions, it could be a sign of a ransomware attack.
- Ransomware message: Ransomware attackers often display a message on the infected PC, demanding payment in exchange for the decryption key. If you see such a message, your PC has likely been infected by ransomware.
- Slow performance: Ransomware can slow down your PC’s performance by using up system resources. If you notice a sudden drop in your PC’s performance, it could be a sign of ransomware.
- Unfamiliar software or processes: Ransomware can install unfamiliar software or processes on your PC. If you see unfamiliar software running or if you notice unusual network traffic, it could be a sign of a ransomware infection.
- Pop-up ads or spam emails: Ransomware attackers often use pop-up ads or spam emails to spread their malware. If you notice an increase in pop-up ads or spam emails, it could be a sign that your PC has been infected.
If you suspect that your PC has been infected by ransomware, it is important to take action immediately to prevent further damage. Disconnect your PC from the internet, and contact a cybersecurity expert or your IT department for assistance.
Are you located Trichy? If yes then check out the -> Cyber Security training in Trichy
Which antivirus can remove Ransomware?
Several antivirus software programs can detect and remove ransomware from an infected PC. However, it is important to note that not all antivirus software is equally effective against ransomware. Here are some antivirus programs that are known for their effectiveness in detecting and removing ransomware:
- Malwarebytes: Malwarebytes is a popular antivirus program that specializes in detecting and removing malware, including ransomware. It uses behavior-based detection and machine-learning algorithms to identify and block ransomware attacks.
- Kaspersky Anti-Ransomware Tool: Kaspersky Anti-Ransomware Tool is a free tool that can protect your PC from ransomware attacks. It uses behavior-based detection to block ransomware attacks in real time.
- Trend Micro: Trend Micro is an antivirus program that offers several anti-ransomware features, including a folder shield, which protects important files and folders from ransomware attacks.
- Norton 360: Norton 360 is a comprehensive antivirus program that includes anti-ransomware protection. It uses behavior-based detection and machine-learning algorithms to detect and block ransomware attacks.
It is important to note that no antivirus software can provide 100% protection against ransomware. Therefore, it is essential to take additional measures, such as regularly backing up your files, keeping your software up-to-date, and being cautious of suspicious emails and links.
To stay secure from Royal Ransomware attacks, it is recommended to follow some best practices, such as:
Royal Ransomware is a serious threat that can cause significant damage to your data and reputation. By following these tips, you can protect yourself and your organization from becoming a victim of this ransomware.
– Avoid opening suspicious emails or attachments from unknown sources
– Keep your system and applications updated with the latest security patches
– Use reliable antivirus software and scan your system regularly
– Backup your important data regularly and store it offline or on a separate device
– Do not pay the ransom or communicate with the attackers, as it may encourage them to continue their malicious activities
– Report any incident of Royal Ransomware attack to the relevant authorities or cyber security experts
Conclusion
To protect against Royal Ransomware and other types of ransomware, it is essential to practice good cybersecurity hygiene. This includes keeping the software and operating systems up to date, using strong passwords and two-factor authentication, and being cautious when opening email attachments or clicking on links from unknown sources. It is also important to regularly back up important files to an external drive or cloud storage service so that they can be easily recovered in the event of a ransomware attack.
Share Post Via
This Guide was Authored by

Suresh Kumar
Cyber security Trainer and Content Creator at Systech Group
Suresh Kumar is a software engineer with over 15 years of experience in the IT industry Certified as an Ethical Hacker (CEH) and has been certified since 2016. He has gained a wide range of knowledge and skills in various areas of the industry, including cybersecurity, network infrastructure, project management, and technical support.

