What Is the Difference Between IPv4 vs IPv6 Addressing?
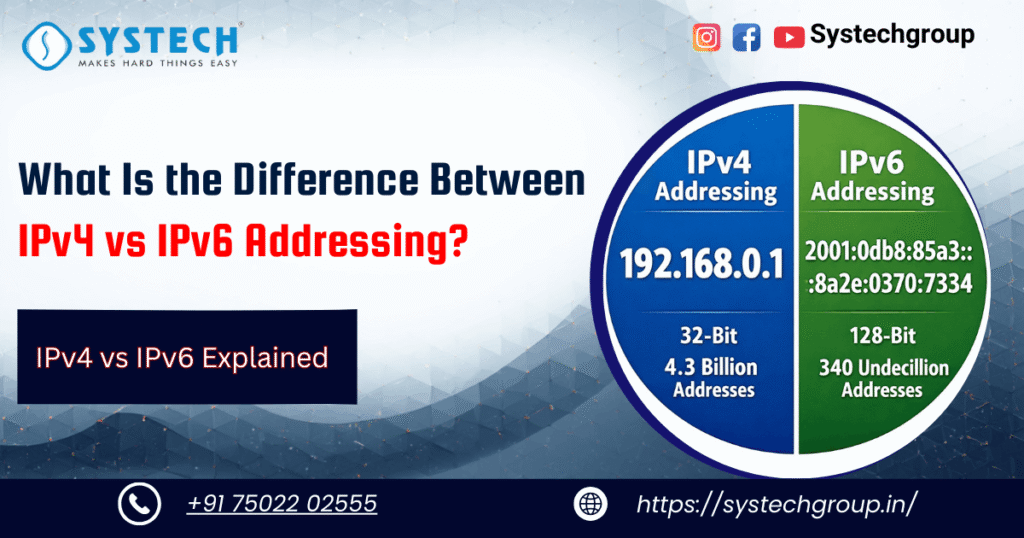
Reading Time: 15 minutesTable of Contents Introduction: New to networking? IP address problems can slow you down quickly. Devices fight for a limited address space, labs stop working, and troubleshooting becomes confusing. This is where understanding IPv4 vs IPv6 addressing makes a real difference. IPv4 is old and running out of space, while IPv6 is new and practically […]
Why Cybersecurity Professionals Are the Backbone of Modern Business

Reading Time: 13 minutesTable of Contents Why Cybersecurity Professionals Matter in Today’s World In today’s hyper-connected world, businesses of every scale rely heavily on digital platforms for operations, transactions, and communication. But this dependence on technology also exposes companies to a rising wave of threats like data breaches, ransomware attacks, and insider risks. The ones standing guard against […]
How to Master Subnetting for CCNA and Networking Success

Reading Time: 11 minutesTable of Contents Introduction Networking can feel overwhelming when you first start preparing for CCNA or other certifications. One of the biggest challenges students face is understanding subnetting. Without solid subnetting skills, you may struggle with IP addressing, routing, and even real-world troubleshooting. The good news is that subnetting is not as scary as it […]
The Security Threats IT Teams Aren’t Talking About

Reading Time: 13 minutesTable of Contents IT security is one of the most important issues in the world right now. Due to the excessive amount of data that is now available digitally, hacks and data theft have become extremely lucrative and widespread. The most common targets of these hacks are companies and data centers. The problem is that […]
How to Tackle the Biggest Cybersecurity Challenges in Today’s Digital World

Reading Time: 11 minutesTable of Contents In today’s digital landscape, cybersecurity challenges are growing in complexity and scale. Businesses and individuals alike face an increasing number of threats that jeopardise data, privacy, and infrastructure. The rise of emerging cyber threats, including AI-powered attacks and cloud security vulnerabilities, calls for robust and proactive defence strategies. Tackling these cybersecurity challenges […]
Python Cybersecurity Applications in Real-World Threat Detection

Reading Time: 12 minutesTable of Contents In today’s world, cyber threats have evolved into complex challenges affecting individuals and organisations alike. Detecting these threats swiftly and accurately is crucial to securing sensitive information and maintaining network integrity. This is why Python cybersecurity has gained significant attention, providing powerful techniques to automate threat detection and response. Many in the […]
How Do You Become a Cybersecurity Expert Without a Tech Degree

Reading Time: 12 minutesTable of Contents Breaking Into Cybersecurity Without a Tech Degree Becoming a Cybersecurity expert may sound like a dream reserved for computer science graduates or people from IT backgrounds—but today, that’s no longer the case. With the rise of online threats and the demand for digital protection, companies need skilled professionals who can focus on […]
What is the Difference Between Vulnerability Assessment and Penetration Testing?
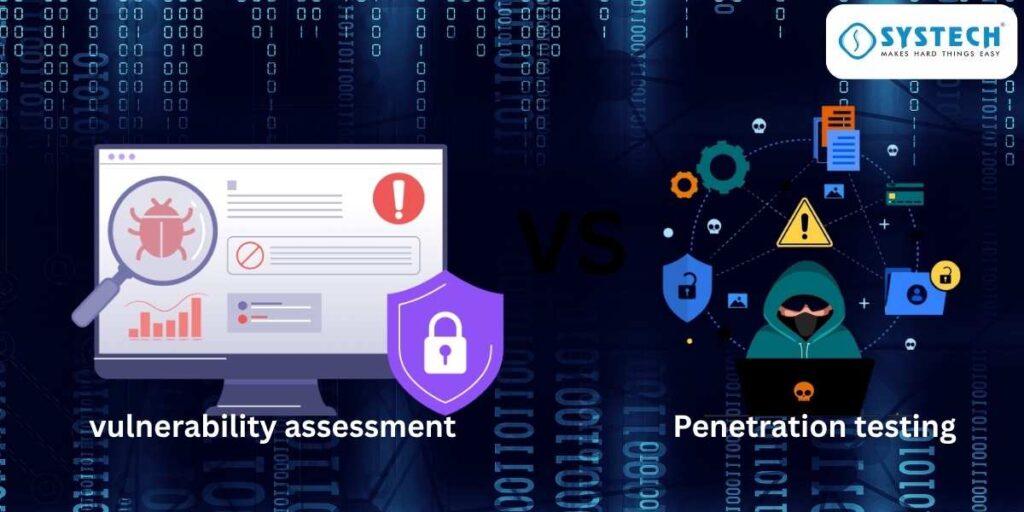
Reading Time: 11 minutesTable of Contents Introduction: Building a successful career in networking or cybersecurity requires more than theory—it demands a clear understanding of critical concepts like vulnerability assessment and penetration testing. At Systech Group, we deliver specialised training in cybersecurity, networking, and ethical hacking with a strong focus on hands-on learning. Through our authorised Pearson and PSI […]
What Is the Cyber Security Salary Per Month in Chennai for Freshers and Experts in 2025

Reading Time: 10 minutesTable of Contents Introduction Are long working hours, job insecurity, and unpredictable pay stalling your career dreams? Cybersecurity professionals in Chennai are rewriting the script—with steady demand, high entry-level salaries, and massive growth potential in 2025. As companies rapidly digitise operations, the need for digital defenders is higher than ever, driving the Cybersecurity salary per […]
Top 20 Trending Software Courses for Beginners and Fresh Graduates

Reading Time: 10 minutesTable of Contents Introduction: Choosing the right career path after studies is never easy. For many beginners and graduates, the biggest challenge is deciding which skills to learn that can truly lead to career growth. With the IT industry evolving every day, employers now seek candidates who can adapt to the latest technologies rather than […]
